General
CONNECT > Configuration > General: The General Configuration page allows the administrator to configure a variety of different options as shown below:
ACR/ACRM Permissions
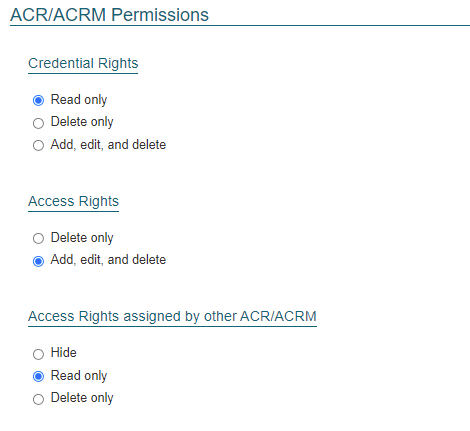
Credential Rights
This section sets the rights that an ACR or ACRM roles have in regards of handling Credentials. The options include:
- Read Only - ACR’s and ACRM’s can view but not edit or delete credentials to an identity
- Delete Only - ACR’s and ACRM’s can view and delete credentials to an identity but not edit
- Add, edit, and delete - ACR’s and ACRM’s have full access to credential management. They can view, add, edit and delete credentials from an identity’s record.
Access Rights
This section sets the relights that an ACR or ACRM roles have in regards handling Access Groups that they own. The options include:
- Delete Only - ACR’s and ACRM’s can view and delete Access Groups to an identity but not edit. Selecting this will force access to be added using the Access Request workflow.
- Add, edit, and delete - ACR’s and ACRM’s have full access to Access Groups management. They can view, add, edit and delete credentials from an identity’s record.
Access Rights assigned by other ACR/ACRM
This section sets the rights that an ACR or ACRM roles have in regards to access groups that are assigned to identities but are not directly owned by the them. The options include:
- Hide - ACR’s and ACRM’s will not be able to see access they do not own
- Read Only - ACR’s and ACRM’s will be able to see all the access groups assigned to an identity but they will only be able to assign or edit access they own
- Delete only - ACR’s and ACRM’s will be able to see and edit all the access groups assigned to an identity but they will only be able to assign access they own
These setting affect the ACR and ACRM roles ability on the CONNECT Identity page.
Identity Manager Permissions
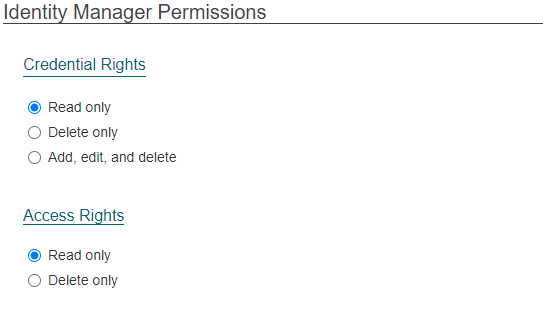
Credential Rights
This section sets the rights that the Identity Manager has with the Credentials associated with the identities they manage. The options include:
- Read Only - The identity manager can view but not edit or delete credentials to an identity
- Delete Only - The identity manager can view and delete credentials to an identity but not edit
- Add, edit, and delete - The identity manager have full access to credential management. They can view, add, edit and delete credentials from an identity’s record.
Access Rights
This section sets the rights that the Identity Manager has with the access groups assigned with the identities they manage. The options include:
- Read only - The identity manager will only be able to see the access that is assigned to the identities they manage.
- Delete only - The identity manager will be able to see and delete the access that is assigned to the identities they manage.
Photo ID Tech Credential Rights
This section sets the rights that a Photo ID technician has with the credentials associated with an identity. The options include:
- Read Only - Photo ID technician’s can view but not edit or delete credentials to an identity
- Delete Only - Photo ID technician’s can view and delete credentials to an identity but not edit
- Add, edit, and delete - Photo ID technician’s have full access to credential management. They can view, add, edit and delete credentials from an identity’s record.

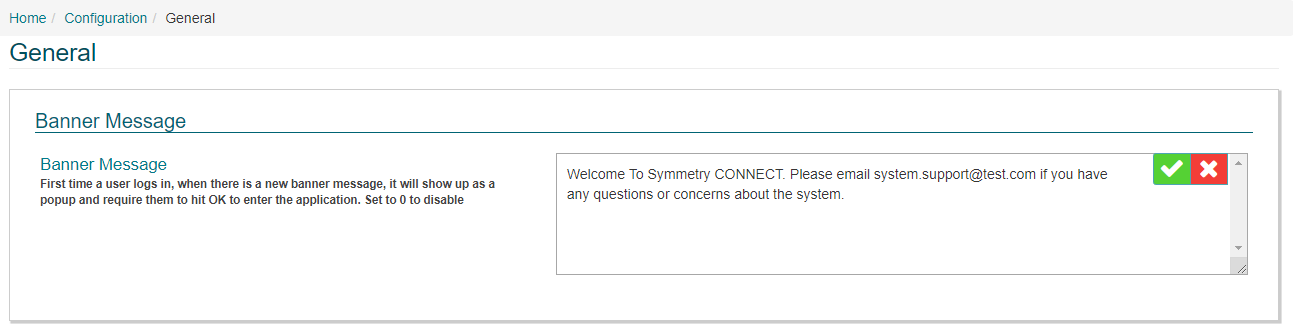
Banner Message:
An administrator can configure the Banner Message, which is seen by all users when they log into CONNECT for the first time.
Role Actions:
This section allows the administrator to specify which User Roles are able to add new Identities via the CONNECT Identities page. If enabled, the specified role will be able to add new Identities into the system.
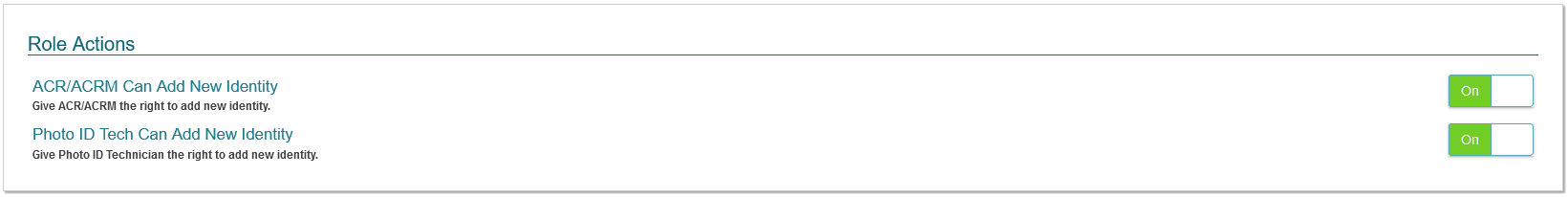
For more information regarding the process of adding a new Identity, please review the Identities section of this guide.
Non-Employee:
This section allows the administrators to configure whether non-employee Identities’ Access Groups and/or Credentials should have an expiration date set automatically when they are added to the record.
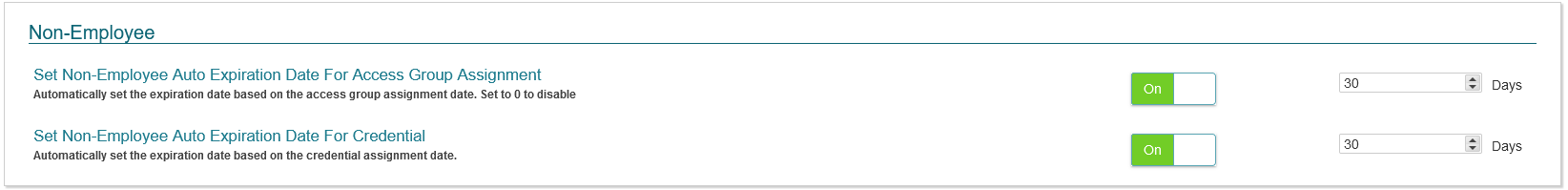
- The image above shows a configuration whereby all non-employee Identities that are created on the CONNECT tab of the system will have their access and credential expiration dates automatically set to 180 days from date of creation.
- When a new credential is issued to a non-employee, or an access right is manually assigned them, an expiration date will be set automatically by the system.
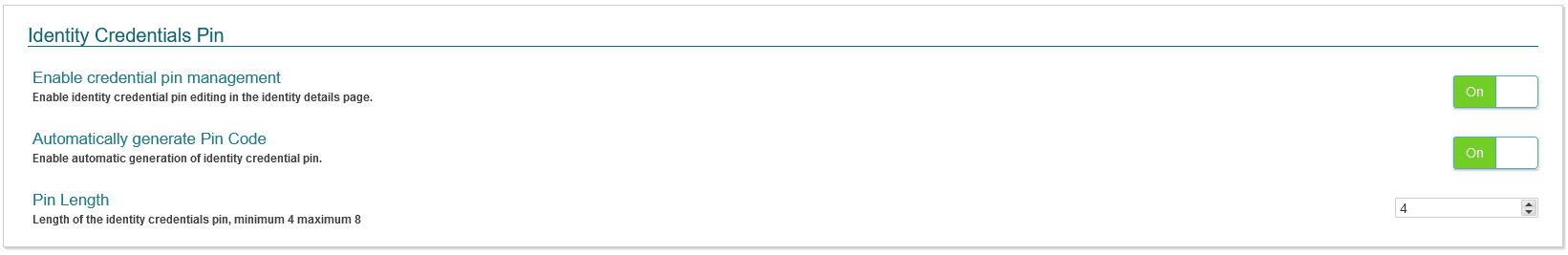
Identity Credentials Pin
This section allows administrators to configure setting regards an identities Pin Code. A Pin Code is a number used by the Identity at specific keypad readers in the Symmetry Access Control System to verify that they are the owner of the card (someone who found/stole the card would not normally know the Pin Code). The Identity presents their card, enters their pin on the keypad and is then allowed access through the door. Options include:
- Enable credential pin management - Enables the configuration of an identity pin code. Options include On or Off.
- Automatically generate Pin Code - When enabled a pin code will be automatically generated when an identity is added. Options include On or Off.
- Pin Length - Specifies the number of digits the PIN code must be.
Manage Pin & IDS Codes via a separate User Role
This section allows for administrators to configure if PIN and IDS code management should be controlled by ACRs and ACRMs or require a separate role to manage. When this setting is set to:
- Off - ACRs and ACRMs will automatically be able to edit the PIN and IDS codes if enabled.
- On - New roles for Pin code Manager and IDS Code Manager will be selectable via the roles management page and allow this permission to be set at a per identity basis.
Use Hotstamp
This section allows for administrators to configure if credentials should be assigned via there card number (Off), or hotstamp (On)
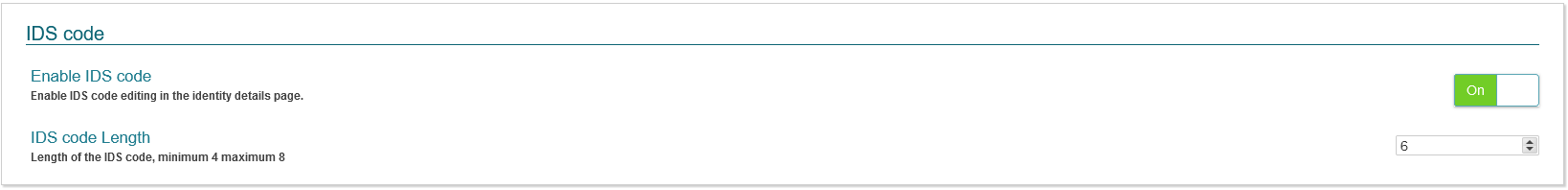
IDS Code
This section allows administrators to configure setting regards an identities IDS Code. An IDS Code (Intruder Detection System) is typically a unique code that an Identity uses to arm/disarm an IDS “Alarm” zone. The Symmetry Access Control System includes some IDS functionality, which requires the Identity to have an IDS Code assigned. Options include:
- Enable IDS code - Enables the configuration of an identity IDS (intrusion detection system) code. Options include On or Off.
- IDS code Length - Specifies the number of digits the IDS code must be.
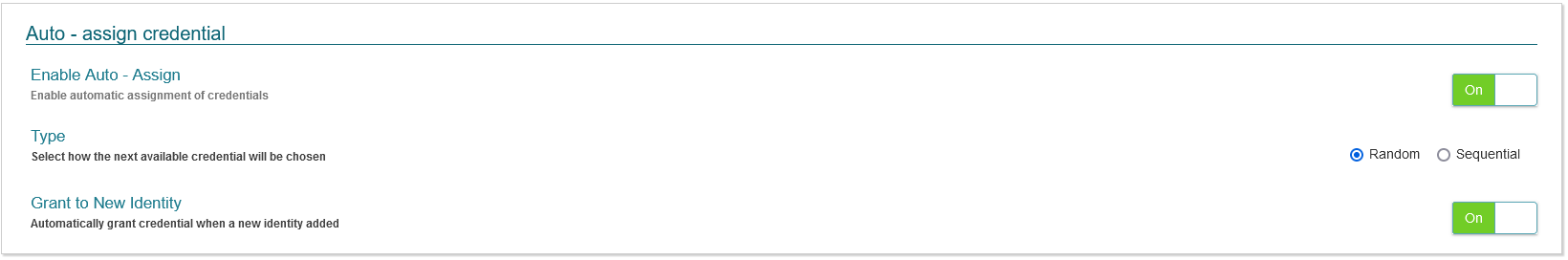
Auto - assign credential
This section allows administrators to configure if and how credentials should be auto assigned. Options in this section include:
- Enable Auto - Assign - Enables credentials to be auto assigned
- Type - Defines how the credentials should be assigned. Options include Random or Sequential
- Grant to New Identity - Enables credentials to be automatically assigned to a new identity
Access Control Rules
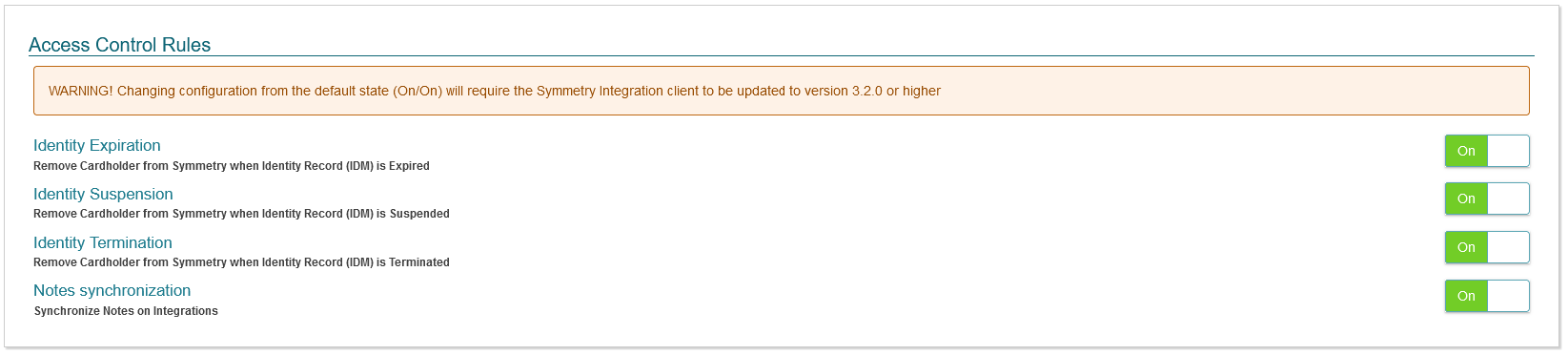 This section allows for an administrator to configure how identities will be handled in the access control system. Options include:
This section allows for an administrator to configure how identities will be handled in the access control system. Options include:
- Identity Expiration - This setting addresses expired identities. When enabled an expired identity will be removed from both CONNECT and the access control system. When disabled, the expired identity will be marked as expired in CONNECT and the access control system. In addition, all access and credentials (except for the last one) will be removed
- Identity Suspension - This setting address suspended identities. When enabled a suspended identity will be removed from both CONNECT and the access control system. When disabled, the suspended identity will be marked as expired in CONNECT and the access control system. In addition, all access and credentials will not be removed.
- Identity Termination - This setting address terminated identities. When enabled a terminated identity will be removed from both CONNECT and the access control system. When disabled, the terminated identity will be marked as expired in CONNECT and the access control system. In addition, all access and credentials (except for the last one) will be removed.
- Notes Synchronization - This settings enables or disables the syncing of notes entered in the CONNECT Identities Notes section with the Card Holder Notes in the Symmetry Access Control system.
Changing configuration from the default state (On/On/On) will require the Symmetry Integration client to be updated to version 3.2.0 or higher
Access Control Synchronization
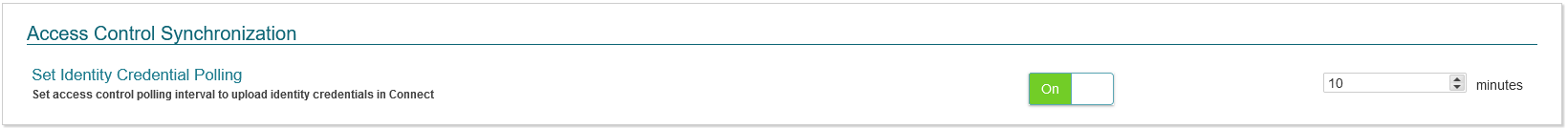 This section allows for administrators to configure settings around how CONNECT will sync with the access control system. Options Include:
This section allows for administrators to configure settings around how CONNECT will sync with the access control system. Options Include:
- Set Identity Credential Polling - This setting will allow for CONNECT to poll for credentials added to an identity in the access control system. This setting can be set to:
- On - Will poll for new credentials added to an identity in the access control system. The rate that this will occur is configurable in minutes.
- Off - Will not look for credential updates to an identity in the access control system.
Access Control Identity Sync
 This section allows for administrators to configure settings for when identities will be send down to the access control system. Options include:
This section allows for administrators to configure settings for when identities will be send down to the access control system. Options include:
- Credential Only - Sends an identity record to all access control systems once a credential is provisioned
- Access Group Only - Sends an identity record to an access control system once an access group is provisioned
- Access and Credential - Sends an identity record when both a credential and an access group is provisioned
- Identity Only - Sends an identity record to all integration on identity creation
Badge Templates
This section allows for an administrator to define a list of badge templates that can be selected and associated with an identity. This badge template will sync to the badge template field in the Symmetry Access Control system. This allows for the badge template to be set in CONNECT, while allowing the badge printing/encoding to be done in Symmetry Access Control.
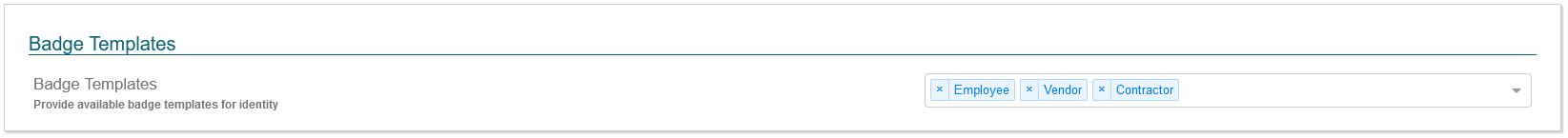
The badge template names entered in this setting must be an exact match for them to sync correctly with the Symmetry Access Control system.
Identity Matching
This section allows for a administrator to enable or disable the ability for CONNECT to attempt to match identities in the access control system via the unique identifier defined in the integrations configuration when it is unable to match via its identityId. This can help prevent duplicate identities being added to the access control system when an identity is directly added to the access control system before it is added to CONNECT.