Rules
CONNECT -> Configuration -> Rules:
CONNECT Rules configuration allows the user to configure rules related to automatic Access Group assignment and expiration. Within this section a user is able to:
-
Create and manage Access Group Rules, which assign Access Groups to various Identities based on their attributes.
-
Configure specific Access Groups to be Auto Approved; if a user requests the Access Group, it is assigned without requiring any approval.
-
Configure rules to automatically suspend Credentials after a specified period of inactivity for specific Identity Types.
-
Configure rules to automatically expire Access Groups after a specified period of inactivity for specific Identity Types.
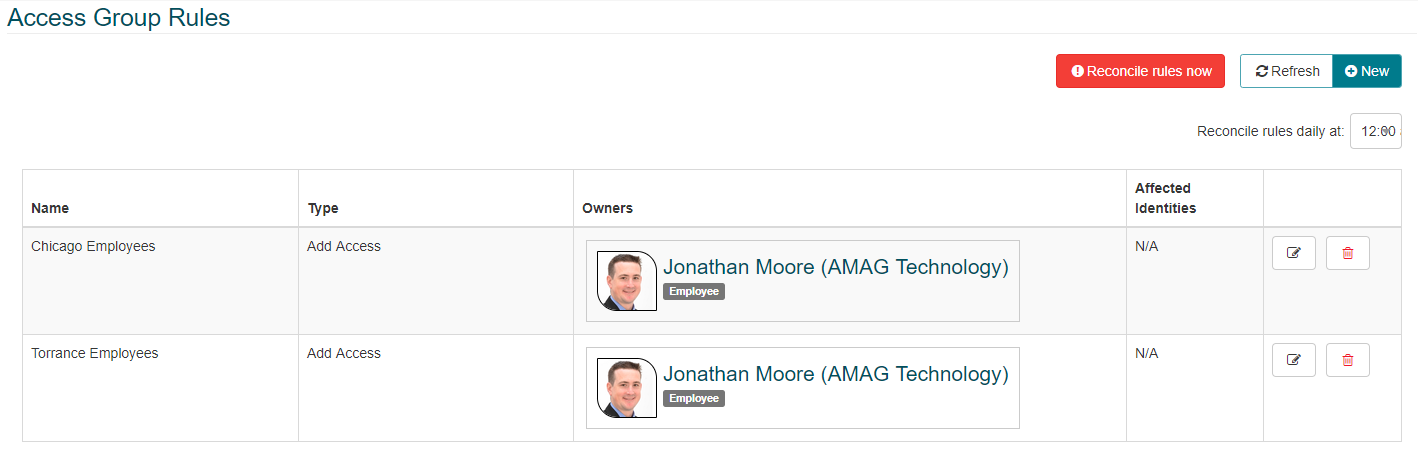
Access Group Rules:
-
Selecting Access Group Rules will display a list of existing rules to the user. The user is able to edit/delete the existing rules if required.
-
“Reconcile rules now” will cause the system to review all existing Identities and ensure they have the correct Access Groups assigned to them per the rules configuration of the system. This process typically occurs daily at midnight (Per the “Reconcile rules daily at:” time configuration).
-
Click “New” to create a new rule.
-
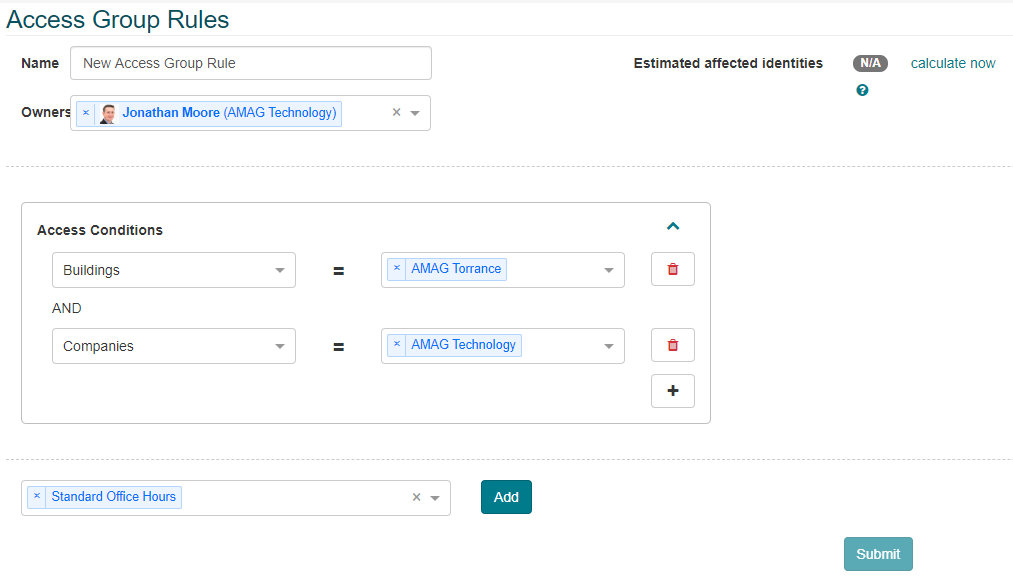
Select an “Owner” of the rule (Note: The owner is simply the person responsible for the rule. Selecting a user as the owner does not provide any additional functionality or access to the user).
-
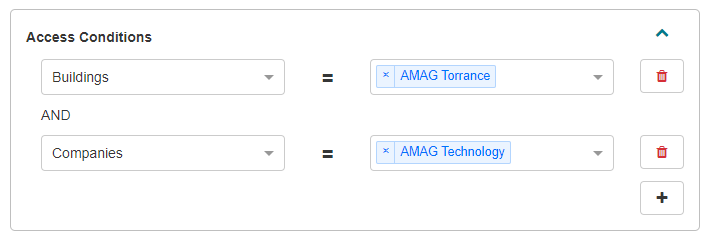
Configure one or more Access Conditions for the rule.
Access conditions determine which Identities apply to the rule. For example, the image below shows Access Conditions for the “AMAG Torrance” Building and “AMAG Technology” Company. Any Identity assigned to this specific Building and Company will be assigned to this rule.
-
Finally, select one or more Access Groups. Any Identities that are assigned to this rule, will have these Access Groups assigned to them automatically by the system.
To see more about Access Groups auto-assigned to Identities please review the Identities section of this guide.
Auto Approve:
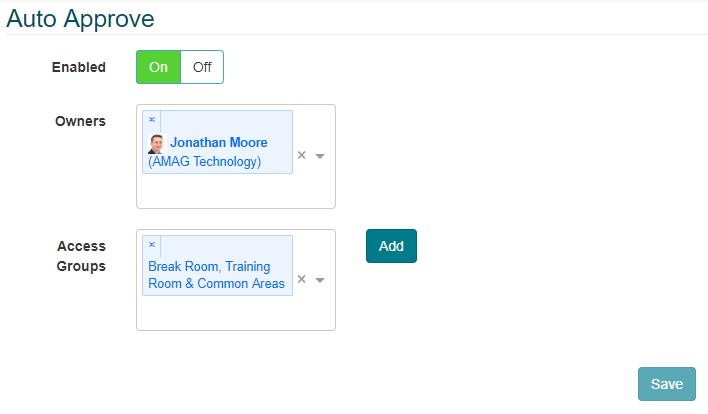
If enabled, auto-approval rules allow specific Access Groups to be configured for automatic approval (i.e. no approval from an ACR or other user is required). Auto-approval rules are intended to be used for lower security areas that don’t require approval, but are not assigned to Identities automatically. Specific use cases include:
-
Areas that are not high-risk, but are not typically assigned to most users.
-
Areas that are auto-assigned by an Access Group rule to local users, but are not assigned to users from a different region.
If an Identity requires access to this area, they simply need to place an access request and the group will be assigned to them automatically. For more information on access requests, please review this section of the guide.
-
The image below shows an auto-approval rule configured in CONNECT.
Multiple Access Groups can be assigned to the auto-approval rule.
Credential Suspension:
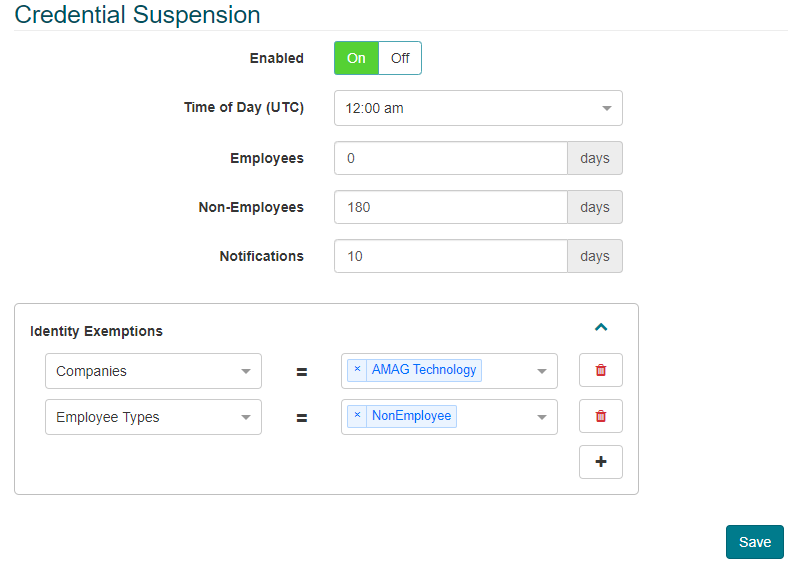
Enabling the Credential Suspension rule will cause access cards assigned to an Identity to expire due to inactivity on the part of the identity. The rule can be filtered by Employees vs Non-Employees, providing a greater level of control over the expirations.
-
If set to “On”, an administrator is able to specify the number of inactive days before the Credential expires for Employees/Non-Employees. If this number is set to 0, the Employees/Non-Employees will never expire.
-
The administrator is able to set the number of days in advance of an expiration that an email notification is sent out.
-
Finally, the administrator is able to configure Identity Exemptions. In other words, the rules apply, except for Identities with specific attributes.
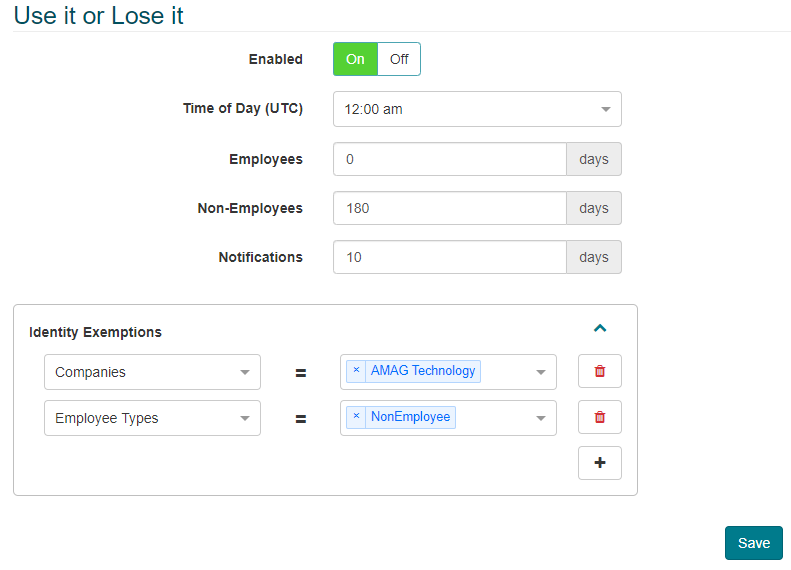
Use it or Lose it:
Enabling the “Use It or Lose It” rule will cause specific access groups assigned to an Identity to expire due to inactivity on the part of the identity. The rule can be filtered by Employees vs Non-Employees, providing a greater level of control over the expirations.
-
If set to “On”, an administrator is able to specify the number of inactive days before the specific Access Group expires for Employees/Non-Employees. If this number is set to 0, the Employees/Non-Employees will never expire.
-
The administrator is able to set the number of days in advance of an expiration that an email notification is sent out.
-
Finally, the administrator is able to configure Identity Exemptions. In other words, the rules apply, except for Identities with specific attributes.