SSO Settings
IDM > Configuration > SSO:
- The Single Sign-On (SSO) service allows users to log in using their existing corporate/domain credentials instead of with a local user name and password managed within the application.
Specific users that may not have SSO credentials can be configured to NOT use SSO. It is highly recommended to have at least one user with local login credentials in case of an issue with the SSO integration.
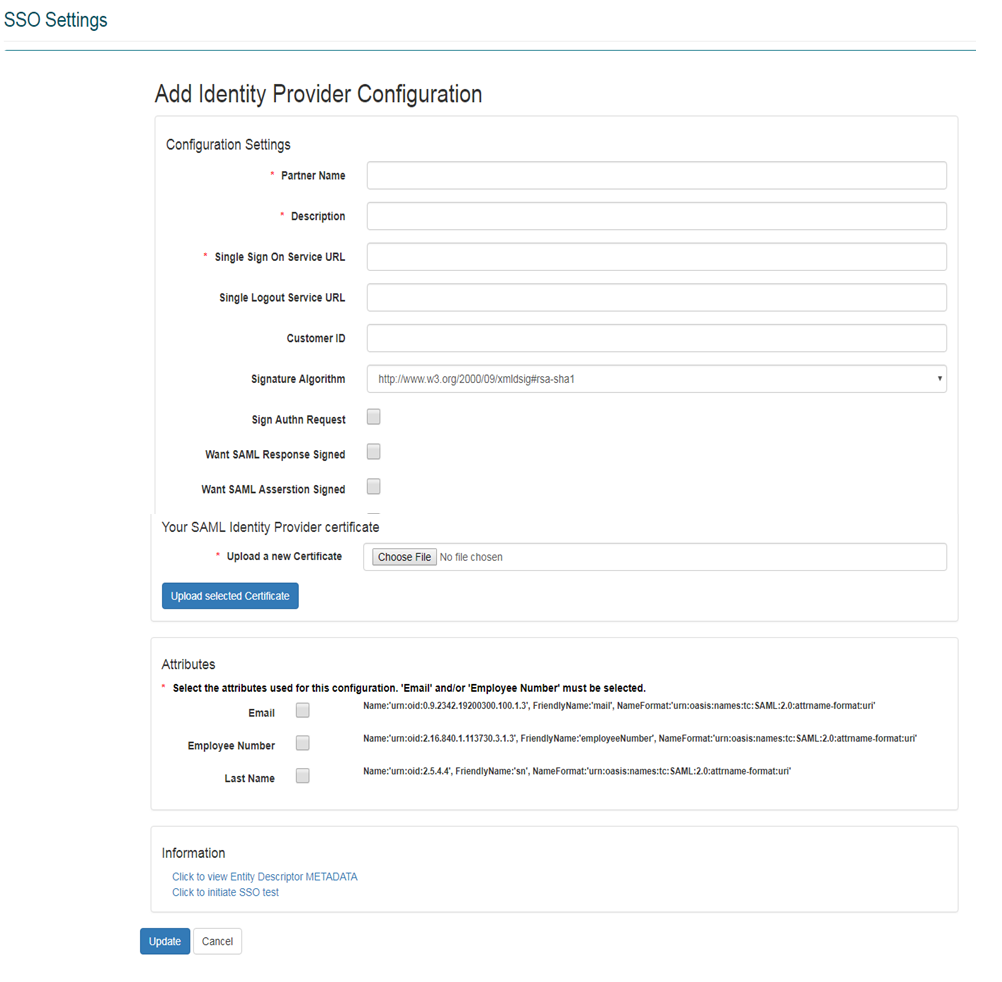
SSO Required Fields
Information:
| Field | Description |
|---|---|
| Partner Name | The value entered here must match the saml:Issuer value provided in the SAML request sent by your Identity Provider. |
| Description | Provide a brief description of the SSO configuration. |
| Single Sign-On Service URL | This is the URL that users will go to initiate the login request. This URL will be provided by your Identity provider. |
| Single Logout Service URL | The location (URL) of your single logout (SLO) service. This is the URL where users will be taken to automatically when they log out of the system. If SLO is not supported, this value can be omitted. |
| Customer ID | Descriptive field used to store additional information about the Identity Provider. This field is not used in the processing of the SAML message. |
| Signature Algorithm | Specify the algorithm used when generating XML signatures to sign SAML assertions provided by your SSO service. If you do not sign SAML assertions, select the default value of ‘http://www.w3.org/200/09/xmldsig#rsa-sha1’. |
| Sign Authn Request | Specifies whether SAML requests sent to your SSO service should be signed. |
| Want SAML Response Signed | Yes/No option specifies if SAML responses received from your SSO service should be signed. If the checkbox is selected, and either the received SAML response isn’t signed or the signature cannot be verified, the response will be considered an error. |
| Want SAML Assertion Signed | Yes/No option specifies if SAML assertions received from your SSO service should be signed. If the checkbox is selected and either the SAML assertion isn’t signed, or the signature cannot be verified the response will be considered an error. |
| Want SAML Assertion Encrypted | Yes/No selection option specifies whether SAML assertions received from your SSO service should be encrypted. If the checkbox is set and either the SAML assertion isn’t encrypted or cannot be decrypted, the response will be considered an error. |
| Your SAML Identity Provider Certificate | The Certificate upload control allows you to upload your SSO service’s public certificate. The certificate uploaded will be used for encryption, decryption and signature verification of SAML assertions, responses made to and received from your SSO service. Once you have your certificate in the correct format, click the certificate control to browse to your certificate file to upload it. If the file is uploaded successfully, the certificate control will be replaced with a button allowing you to remove/replace a certificate for the SSO Configuration. |
Attributes:
| Field | Description |
|---|---|
| Email/Employee Number/Last Name | The Attributes list specifies the User attribute values that will be released in the SAML assertion which is sent from your SSO service to the system. Currently Email and/or Employee Number must be provided as attributes in the SAML assertion from your SSO service, and Email or Employee Number must be selected as attributes on the SSO Configuration. Last Name can only be used in conjunction with Email/Employee Number; it is not a supported attribute on its own. |
Information:
| Field | Description |
|---|---|
| Click to view Entity Descriptor METADATA | Clicking this link will display the XML Metadata for the Entity Descriptor. |
| Click to initiate SSO test | Clicking this link initiates a test of the SSO configuration. |